Introduction
Before we start, let’s take a look at this exploit: CVE-2016-7545. It was reported against SELinux sandbox back in 2016. The malware program inserts some text in the terminal input buffer, and when the program is closed, the shell grabs the text and runs it as a command. Pretty nifty! When the payload hits, the malware program is nowhere to be found. They can even push it in a crontab to run at midnight.
Months later we found the same exploit in Firejail (CVE-2016-9016), only to surface in bubblewrap (CVE-2017-5226) a year later. The problem is the Linux kernel has very little visibility to what’s happening in the user space. It can only react when the application tries to access a file (SELinux, AppArmor), when the app does a system call (sandboxes), or when a network packet enters the system (firewall). For the kernel, the app is just a number of memory segments and CPU time slices. The way applications interact with each other is of no concern.
And then you have the case of client-server applications. The user sandboxes the client and the real work is done outside the sandbox on the server. One such example is the multi-tab terminal emulators. You sandbox gnome-terminal and you would expect your commands are running in the sandbox – WRONG! The sandboxed client is only the nice graphical user interface you see on the screen. You can change the size, the fonts, the colors… but the commands are executed by a server process outside the sandbox.
All multi-tab terminal emulators work this way, don’t attempt to run them under something like Firejail or AppArmor. This type of program operates by default in sandbox escape mode!
Features
Firajail provides native support for AppImage applications. These are the main features of AppImage/Firejail combo:
- state of the art software packaging and seccomp/namespaces sandboxing technology
- network and X11 sandboxing support
- monitoring and auditing capabilities
- low runtime overhead, no daemons running in the background, all security features are implemented in Linux kernel
- it can be used in parallel with other security frameworks such as AppArmor, SELinux
Usage
I download the appimage from LibreOffice site, and copy it under /opt as root. This way, regular users cannot temper with it. I use –appimange command line option to start the sandbox:
$ firejail --appimage /opt/LibreOffice-fresh.basic-x86_64.AppImage
Reading profile /etc/firejail/libreoffice.profile
Reading profile /etc/firejail/allow-java.inc
Reading profile /etc/firejail/disable-common.inc
Reading profile /etc/firejail/disable-devel.inc
Reading profile /etc/firejail/disable-exec.inc
Reading profile /etc/firejail/disable-passwdmgr.inc
Reading profile /etc/firejail/disable-programs.inc
Reading profile /etc/firejail/whitelist-var-common.inc
Parent pid 9299, child pid 9302
Mounting appimage type 2
...
Based on the name of the appimage archive, Firejail tries to find a suitable profile for the application. It found /etc/firejail/libreoffice.profile, which is the regular security profile for LibreOffice. If no such profile is found, the sandbox will use the default profile in /etc/firejail/default.profile. This is a very restrictive profile, believed to work in most situations. Anyway, once started you can do a short check on ~/.ssh or ~/.gnupg directory:
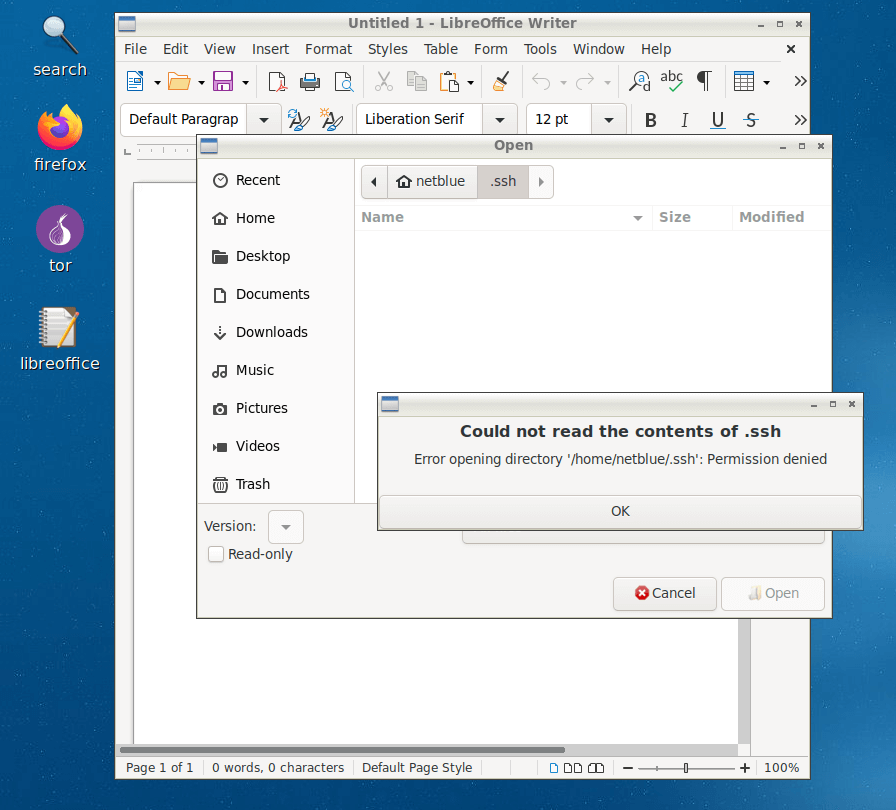
Then, I configure a desktop starter – libreoffice icon in the picture above. The starter is a regular text file in ~/Desktop directory:
$ cat ~/Desktop/libreoffice.desktop
[Desktop Entry]
Name=libreoffice
Exec=/usr/bin/firejail --appimage /opt/LibreOffice-fresh.basic-x86_64.AppImage
Icon=/usr/share/icons/nuoveXT2/48x48/apps/text-editor.png
Terminal=false
Type=Application
You can add more sandboxing options on the exec line, or you can build a custom profile for it as explained here.
Conclusion
Easy to use, AppImage is a very convenient way to try new software before you include it in your daily routine. Many open source project developers are making appimages available, and depending on your Linux distribution, this could be the only way you can upgrade a program to a newer version.
Just keep in mind, some programs cannot be sandboxed, and exploits can surface any time. Kernel-based security technologies such as Mandatory Access Control and sandboxes have their own limitations. If for any reason you don’t trust the people distributing an appimage, or any other binary executable for that matter, don’t install it on your computer!
More info:
- AppImage project home: http://appimage.org/
- For developers: https://github.com/probonopd/AppImageKit
- Documentation: https://github.com/probonopd/AppImageKit/wiki
- Application repository: https://www.appimagehub.com

